Advances in technology undoubtedly bring us convenience and seemingly endless possibilities. Yet, lurking behind these benefits is a dark and unnerving reality – the vulnerability of precious data. Cyber breaches have become a widespread phenomenon, threatening not only our privacy but also the stability of businesses and even governments.
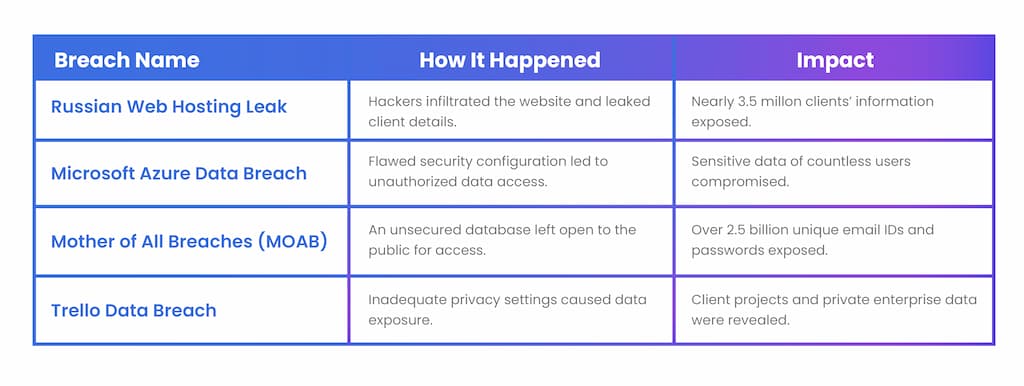
As we continue to live in this ever-connected digital age, they pose an impending danger we cannot afford to ignore. This article builds on a previously published post, 'Four Costly Cyber Breaches That You've Already Forgotten About', by delving deeper into four specific incidents: the Russian Web Hosting Data Leak, Microsoft Azure Data Breach, the Mother of All Breaches (MOAB), and the Trello Data Breach.
"We can't solve problems by using the same kind of thinking we used when we created them."
— Albert Einstein
Russian Web Hosting
If you imagine your data as your confidential letters stored in a post office, a data breach is a bit like someone breaking in and going through those letters. Now, with that in mind, let's tackle the term 'Russian Web Hosting Leak'.
Firstly, "web hosting" is similar to the post office where you keep those letters, only in this case, it's a service allowing organizations and individuals to post websites or web pages onto the Internet. In our scenario, the post office (web hosting service) is located in Russia.
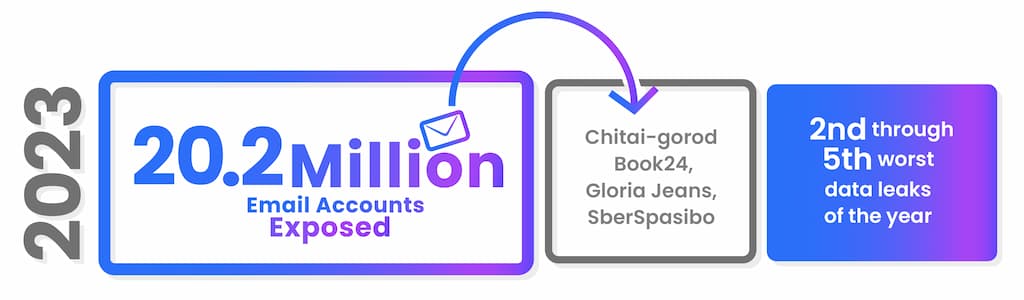
Now, in 2023, four seemingly-safe storage lockers (think of them as big brands, namely Chitai-gorod, Book24, Gloria Jeans, and SberSpasibo) were compromised. This resulted in the 2nd through 5th worst data leaks of the year. The 'leak' saw troubling figures of over 20.2 million 'letters' (email accounts) exposed in these breaches.
It's also worth noting that more than half of big-scale cyberattacks originate, not surprisingly, from Russia. This doesn't directly imply that Russian folk are the bad guys, but it does constitute a pattern that's crucial for understanding global cybersecurity trends.
Last but not least, when you look at the percentage perspective, a large chunk of these breaches arise from poorly coded web applications. It means our beloved lockers (web hosting services) are mostly cracked open due to errors left in their locking mechanisms (their web codes).
In sum, if you're a resident of Russia or use any services hosted in the region, your 'letters' (personal data) might not be as secure as you think. It's always a good idea to recheck who is handling your data and how securely it is being managed.
Microsoft Azure

What if you stored your most prized possessions in a supposedly secure storage lockup, then one day you discover that the security officiator made a mistake. The keys to your lockup have been misplaced, and your treasured items have been exposed to countless strangers.
This pretty much encapsulates what happened with the Microsoft Azure data leak.
The experts at Microsoft Azure who are entrusted to protect the data 'lockup', unknowingly left the doors open. This mishap, a result of a cloud misconfiguration - identified by the NSA as the most dangerous cloud vulnerability - led to a severe data breach. Essentially, the coding equivalent of losing your keys (but way worse.)
A wide array of personal and sensitive data was exposed, up for grabs to those with malicious intent. This data breach goes on to show that even the biggest players in the industry are susceptible to mistakes. With over 80% of data breaches in 2023 involving data stored in such cloud platforms, it underscores the need for rigorous data protection measures.
The most crucial takeaway from this incident?
The time it takes to unearth and contain breaches like these. The fact that breaches involving misplaced credentials often take as long as 328 days to recognize and contain amplifies the magnitude of this problem. And not to mention, the untold repercussions for the millions of users whose exposed data can end up in the wrong hands.
So, the Microsoft Azure data leak was more than just a breach. It was an urgent wake-up call for enhanced cybersecurity measures and stricter vigilance in the digitized, cloud-based era we've entered.
MOAB
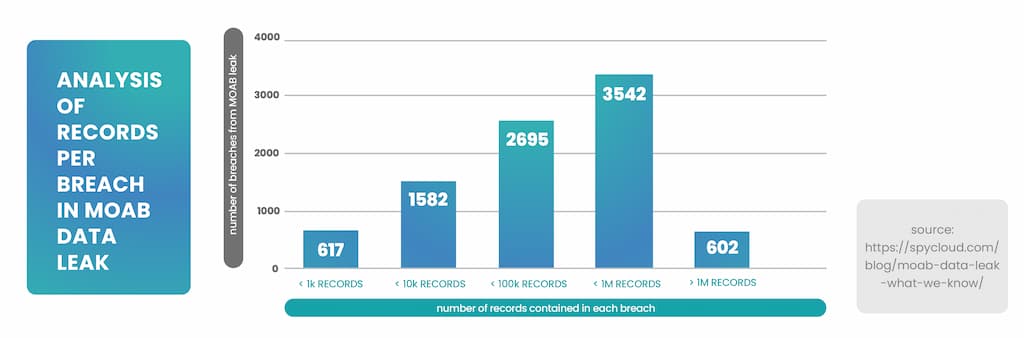
https://spycloud.com/blog/moab-data-leak-what-we-know/ (graphic source here)
With this breach, the culprits managed to get unauthorized access to a vast array of private information, shaking the digital world. It wasn't just about the volume of the information that was compromised, but about the sheer audacity of it.
To understand the magnitude of this attack, visualize a city like New York's Manhattan being emptied of all its residents. It would be pretty shocking, wouldn't it? Now, imagine that instead of residents, we're talking about individual pieces of sensitive digital data. That's how staggering the scope of the MOAB was.
Victims of the breach found themselves in a precarious scenario where their personal, financial, and even professional data were potentially being misused. The level of potential damage from the breach extends far beyond individual users. Information leaks at this scale can impact national security, lead to corporate espionage, and even fuel illicit activities on the dark web.
This notorious breach should serve as a wake-up call: there's a need for stronger data safety measures in our increasingly interconnected world.
As we go forward, it's crucial to you, as an internet user, to be accountable for your digital footprint. Think twice before sharing personal information on digital platforms, and continuously review and reinforce your security settings. After all, in the world of cyber security, being proactive is often the best defense.
Trello

Now, let's talk about Trello.
Trello, if you're not familiar, is a popular web-based project management application. It's like an online whiteboard filled with lists of sticky notes, which can be moved around between different lists. It's a great tool for organizing projects, delegating tasks, or just keeping track of daily to-dos. But imagine the shock when Trello users discovered that their precious sticky notes, in digital terms their data, had been breached.
Despite its seemingly simple and user-friendly interface, behind the scenes, Trello became a hotbed for cyber intrusion. In essence, there was a data leak, meaning unauthorized individuals gained access to sensitive, protected, and private data. Remember how we mentioned that 57% of users reported having a password written down on a sticky note? Well, imagine if those sticky notes were digital and accessible to cybercriminals - a truly alarming prospect.
So what happened during this breach, you may ask?
Cybercriminals exploited vulnerabilities in the security system. Their primary aim, as always, was to gain unauthorized access to data - in this case, confidential project details, personal notes, user profiles, and more. It was a sophisticated operation, with the potential to, and I kid you not, disrupt entire businesses. Given that Trello is used by individuals and corporations alike, the impact of this breach was wide-reaching and significantly damaging.
What could've been done to prevent this?
Well, this is where the unified, AI-powered approach to threat hunting and faster response to threats comes thundering in like a superhero. Leveraging advanced technologies and improved cyber defense strategies, these kinds of breaches can be mitigated. Unfortunately, at the time, Trello didn't have this protective shield. So, the damage was done, and it hit hard.
In conclusion, the Trello data breach was an unfortunate but largely preventable incident. It serves as a wake up call to all digital platform users - security should never be taken for granted. Even our beloved digital sticky notes aren't safe unless protected by robust cybersecurity measures.
Learning from Mistakes: How Companies Can Respond to Data Breaches

When a data breach happens, it's natural to panic. Data breaches can lead to financial losses, damaged reputations, and upset customers. But as much as 95% of these breaches are due to human error. How your company responds to a data breach makes all the difference in your recovery process.
Post-data breach response strategies often focus on addressing the immediate threat, rectifying damages and strengthening defenses. Let's take a look at some concrete steps companies can take after a data breach.
- Identify and Contain the Breach: The first step is to pinpoint how the breach happened and to contain it to prevent further damage. If we consider the average of 233 days it takes for financial services to detect a data breach, there's plenty of room for improvement.
- Assess the Impact: Identifying the types of data compromised and the potential impact on both the company and its customers is crucial. This can include financial loss assessments, potential legal implications, and reputation damages.
- Communicate Responsibly: It's essential to communicate responsibly with stakeholders after a breach, acknowledging the situation and taking ownership. This strategy can help mend customer relationships as transparency builds trust - a handy note considering that 59% of consumers would avoid a company that has suffered a data breach in the past year.
- Improve Security Measures: Data breaches aren't just warnings; they are opportunities to learn and improve. They expose vulnerabilities, providing a chance to strengthen security measures. Companies can and should leverage technologies like AI and machine learning, which 26% of businesses are already using, to predict and handle breaches.
Responding to a data breach effectively can help minimize damage and restore trust. It can also be a wake-up call for companies to invest in data-breach insurance coverage, with one in three US companies having done so.
Regardless of how grave the situation may appear, remember—the most valuable lessons often come from the biggest mistakes. It's how we respond to these mistakes that shape us and, in this case, protect our businesses from future threats.
The Role of Cybersecurity in Preventing Data Breaches
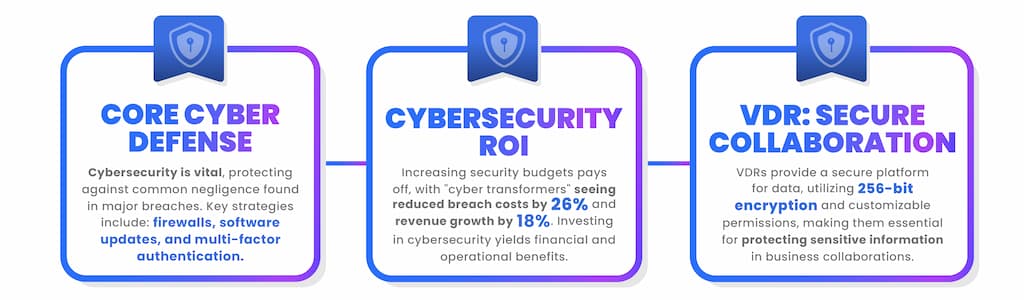
Think about it, cybersecurity isn't just a buzzword, it's an integral part of your company's defense mechanism. If we look into significant data breaches like Russian Web Hosting, Microsoft Azure, MOAB, or Trello, one common thread is negligence or underestimation of cybersecurity measures. Here's where a strong cybersecurity strategy steps in, acting as your first line of defense.
And what is a stronger shield than a combination of proactive planning, robust practices, and the use of secure technologies? We're talking about tools and measures such as firewalls, routine software updates, strict password policies, multi-factor authentication, and so much more.
In the wake of these escalating cyber threats, businesses are bolstering their security budgets and rightly so. Averting a cyber-attack is always cost-effective as opposed to managing one. In fact, "cyber transformers" have reported 26% lower costs from breaches and an 18% increase in revenue growth. Isn't it time to make cybersecurity your priority?
One such advanced, yet underutilized tool in the cybersecurity ecosystem is a virtual data room (VDR). Think of it as your personal safety vault online. VDRs offer an extra layer of protection by providing a secure and controlled environment for storing and sharing sensitive data. The use of 256-bit encryption, two-factor authentication, customizable permissions, and remote document shredding make it ultra-secure and impenetrable to unauthorized access.
Remember, it's not just about securing your own systems but also about assessing the cybersecurity posture of your third parties.
By 2025, it's estimated that 60% of organizations will use cybersecurity risk as a key factor when sealing transactions and business engagements.
Use VDRs to store, share, and collaborate on confidential documents with external entities without the risk of data breaches.
Remember, cybersecurity is an ongoing process. It's not a case of 'set up and forget'. It's important to continually educate your teams, audit your practices, and upgrade your technology. For, as the saying goes, better safe than sorry.
