An API, or Application Programming Interface, is a set of rules and protocols that allows different software applications to communicate and interact with each other. It serves as an intermediary, enabling one application to request and exchange data or functionality with another, often across the internet.
APIs define the methods and data formats that developers can use to interact with a particular software system, abstracting the underlying complexity and allowing for seamless integration between different services, platforms, or components.
APIs are essential in modern software development, powering everything from web and mobile applications to IoT devices, enabling developers to leverage the capabilities of existing software and create new applications that can interoperate with a wide range of services and systems.
Today, every modern enterprise is heavily reliant on APIs, to the point they're now indispensable. As evidence, API traffic now represents over 80% of the current internet traffic. However, with the growing reliance on APIs, a new and concerning trend has emerged – the rise of API breaches.
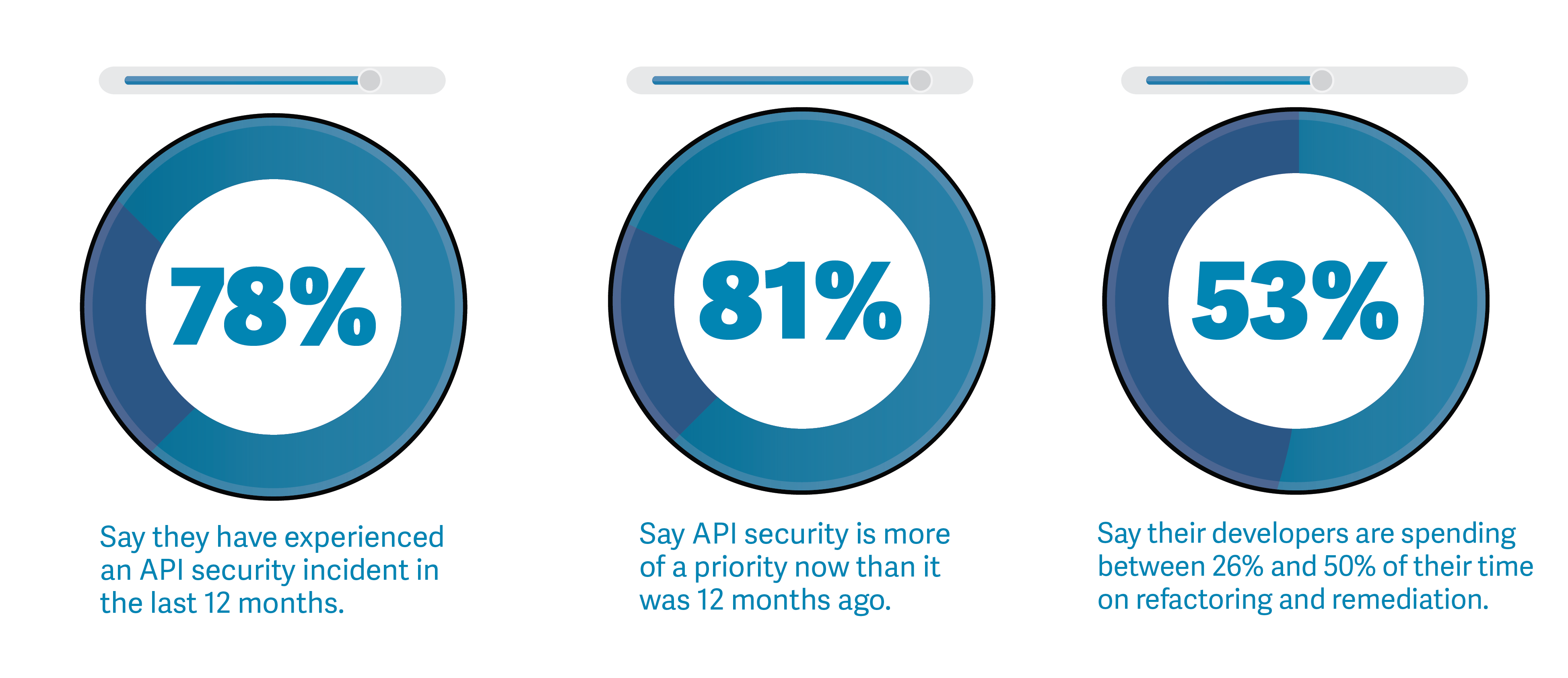
According to a survey conducted by Noname Security, 78% of cybersecurity professionals say they have experienced an API security incident in the last 12 months. These incidents pose serious security risks and have far-reaching consequences for individuals, businesses, and even entire industries.
Understanding API Breaches
API breaches occur when unauthorized individuals or systems gain access to sensitive data or functionality through an API. These breaches can take various forms, including:
Data Exfiltration: Hackers exploit vulnerabilities in APIs to access and steal sensitive data, such as personal information, financial records, or intellectual property.
Distributed Denial of Service (DDoS) Attacks: Attackers overwhelm an API with excessive traffic, rendering it unusable for legitimate users. This can lead to service disruptions and financial losses.
Credential Theft: Hackers use API vulnerabilities to steal authentication credentials, allowing them to impersonate legitimate users and gain unauthorized access to systems and data.
Malicious Code Injection: Attackers inject malicious code or payloads into API requests, potentially compromising the integrity of the underlying systems.
API Key Compromise: API keys, which are often used for authentication, can be stolen or leaked, granting unauthorized access to APIs.
The Soaring Frequency of API Breaches
The frequency of API breaches has been on the rise for several reasons:
Proliferation of APIs: As businesses increasingly rely on cloud-based services and microservices architecture, the number of APIs has exploded. With more APIs in use, the attack surface has grown substantially.
Inadequate Security Practices: Many organizations fail to implement robust security measures for their APIs, making them vulnerable to exploitation. This includes insufficient authentication and authorization controls, lack of encryption, and poor monitoring.
Third-Party Dependencies: Businesses often integrate third-party APIs into their applications, trusting these external services with their data and functionality. However, third-party APIs can be a weak link in the security chain, as organizations have less control over their security practices.
Sophisticated Attack Techniques: Hackers are becoming more sophisticated in their methods, constantly evolving to exploit new vulnerabilities and bypass security measures.
The Impact of API Breaches
API breaches can have devastating consequences:
Financial Loss: Breaches can lead to direct financial losses, including fines, legal fees, and remediation costs. Additionally, reputational damage can result in lost customers and revenue.
Data Privacy Violations: Breaches involving personal or sensitive data can lead to legal and regulatory consequences, such as non-compliance with data protection regulations like GDPR or CCPA.
Service Disruptions: DDoS attacks and other API breaches can disrupt services, causing downtime and frustration for users.
Intellectual Property Theft: Breaches can result in the theft of intellectual property, undermining a company's competitive advantage and innovation efforts.
Solutions and Best Practices
To mitigate the risks associated with API breaches, organizations should adopt a proactive approach to API security:

Implement Strong Authentication: Use robust authentication methods like OAuth2 and API keys with appropriate access controls.
Authorize with Precision: Implement fine-grained authorization controls to restrict access to API resources based on user roles and permissions.
Encrypt Data: Ensure that data transmitted over APIs is encrypted using secure protocols like HTTPS.
Thorough Testing: Regularly assess API security through penetration testing, vulnerability scanning, and code reviews.
Monitor and Audit: Implement real-time monitoring and auditing of API traffic to detect and respond to suspicious activities promptly.
API Rate Limiting: Use rate limiting to protect against DDoS attacks by limiting the number of requests from a single IP address.
Third-Party Risk Management: When using third-party APIs, assess their security practices and ensure they align with your organization's security standards.
The rise of API breaches underscores the critical importance of API security in today's digital landscape. A Virtual Data Room (VDR) can significantly enhance API security by providing a secure and controlled environment for managing API-related documentation, access, and communication.
With APIs playing a pivotal role in modern software ecosystems, the need for robust security measures is paramount. VDRs offer a centralized platform where organizations can securely store API documentation, including authentication protocols, encryption methods, and access controls.
This centralized repository ensures that sensitive API information is only accessible to authorized personnel, reducing the risk of data breaches and unaut horized access. Moreover, VDRs facilitate secure collaboration among development teams, allowing them to share API-related files and updates while maintaining strict access controls.
In addition, VDRs often provide audit trails and granular permissions, enabling organizations to monitor API-related activities and ensure compliance with security policies and regulations. Overall, VDRs play a crucial role in fortifying API security by providing a secure, collaborative, and transparent environment for managing API-related assets.
As APIs continue to proliferate and evolve, organizations must prioritize security by implementing best practices, staying informed about emerging threats, and fostering a culture of security awareness. Failure to do so can lead to financial losses, reputational damage, and legal consequences that no business can afford to ignore.
ShareVault has been providing organizations of all types and sizes with secure document sharing solutions for over 15 years.
