Mergers and Acquisitions (M&A) is a challenging business activity. The M&A process typically spans six months to two years and requires intensive collaboration among buyer and seller teams who perform secure document sharing, due diligence and negotiate the terms of the deal.
M&A due diligence and negotiations require access and secure document sharing of confidential items that define the financial and legal status of the companies and assets involved in the deal. As experienced investors and CEOs know, most—70 to 90 percent—of M&A deals fail, so rigorous due diligence must go beyond the bottom line numbers to provide a clear picture of a target company’s health.
These financial records create security vulnerabilities. Today’s hackers have a sophisticated knowledge of finance, and use AI-enhanced algorithms to seek out vulnerabilities in unencrypted archived records, data banks, and confidential documents shared in emails, consumer-grade file sharing apps, and other under-protected online environments.
Key M&A Document Security Risks
With so many documents involved, M&A has a host of document security risks:
Information leakage
During M&A negotiations, sensitive and confidential information is shared between the involved parties. The risk of information leakage is high, and it could lead to insider trading, competitive intelligence gathering by rival companies, or reputational damage.
Cybersecurity vulnerabilities
Each company can have different cybersecurity protocols, and the integration of systems and networks can introduce new vulnerabilities. Cyber attackers may target the weaker security infrastructure, leading to data breaches, data theft, or disruption of operations.
Data privacy and compliance issues
Merging companies may have different data privacy regulations and compliance requirements. Mishandling personal data or non-compliance with data protection laws can result in legal consequences and damage the reputation of the new entity.
Intellectual property (IP) protection
The M&A process may involve the transfer of valuable intellectual property rights. Failure to adequately protect IP during the transition can result in IP theft or disputes with competitors.
Insider threats
M&A processes often lead to changes in roles and employee structures. Disgruntled employees or those with malicious intent may exploit the confusion to engage in unauthorized activities, steal data, or sabotage systems.
Third-party risks
Merging companies might have different relationships with third-party vendors and contractors. Vendors, contractors, and other third parties can introduce new risks if their security measures are not properly managed.
Compliance and regulatory risks
Mergers and acquisitions can result in a complex web of regulatory requirements, particularly in highly regulated industries like finance, healthcare and the life sciences. Failure to comply with relevant laws and regulations can lead to fines, penalties, and/or legal actions.
Collaboration Channels Increase Security Vulnerabilities
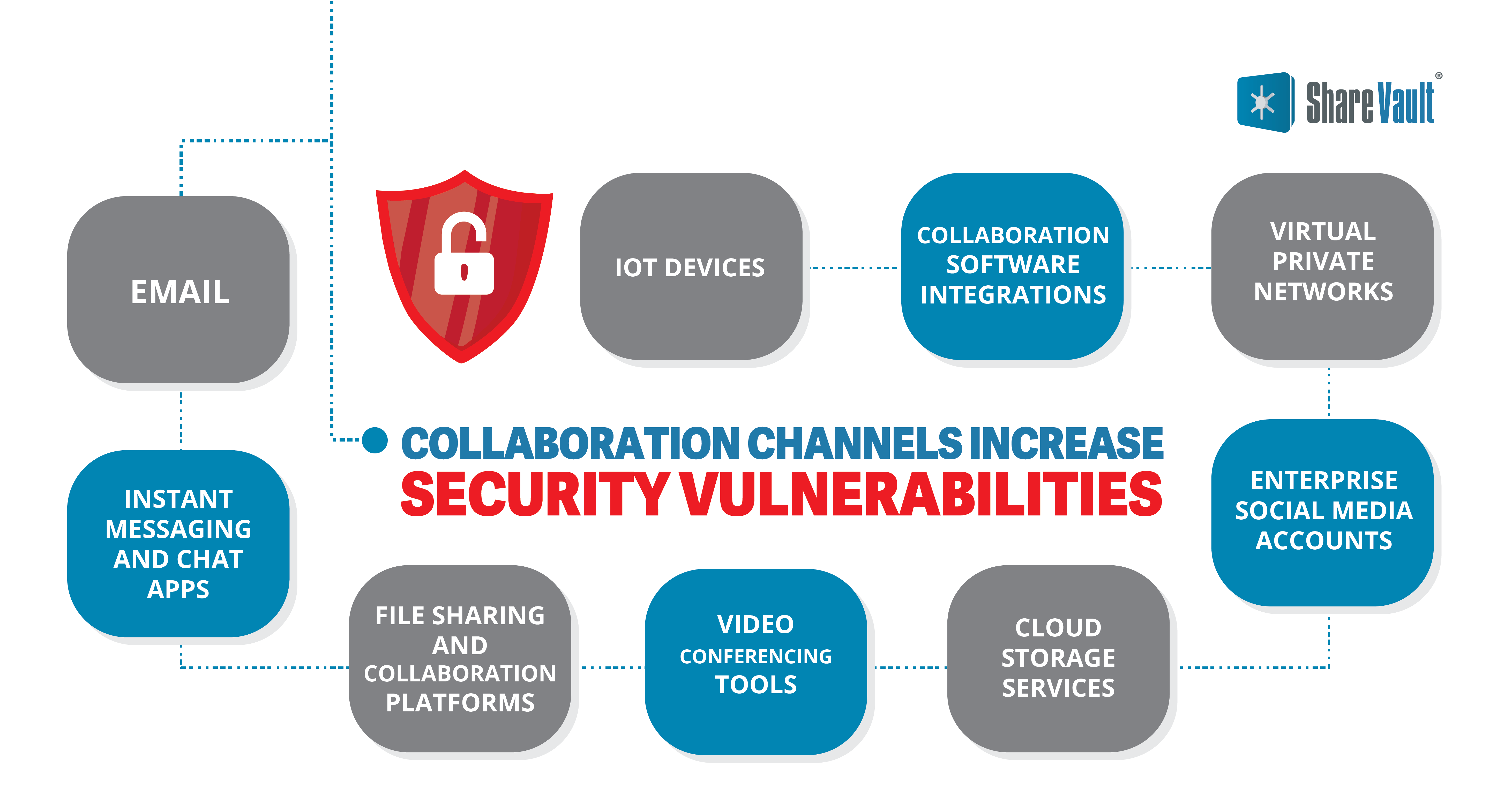
During the many months of due diligence and negotiations, buyer and seller teams routinely share confidential documents internally and with internal and external analysts, lawyers, accountants, and subject matter experts.
While security best practices recommend encryption of all confidential documents and storage in a virtual deal room, time pressures to get a deal on the table can lead to use of communication channels that lack enterprise-grade security, including:
Email is a common target for hackers due to its widespread use. Phishing attacks, where hackers impersonate legitimate entities to trick users into revealing sensitive information, are prevalent in email.
Instant Messaging and Chat Apps
Instant messaging platforms and chat applications have security weaknesses that can be exploited by hackers. This includes unauthorized access to chat logs, files, and attachments shared within the app.
File Sharing and Collaboration Platforms
Cloud-based file-sharing and collaboration platforms are vulnerable if user accounts are not adequately protected, leading to unauthorized access to sensitive documents.
Video Conferencing Tools
Video conferencing platforms can be susceptible to hacking if not properly configured or secured, potentially leading to unauthorized access to meetings and conversations.
Cloud Storage Services
If cloud storage services are not properly secured, hackers can gain access to stored files, compromising sensitive data.
Enterprise Social Media Accounts
Social media accounts used for business purposes can be targeted by hackers for data breaches or spreading misinformation.
Virtual Private Networks
(VPNs): Unsecured VPN configurations expose business networks to potential breaches and unauthorized access.
Collaboration Software Integrations
Third-party integrations used in collaboration software can introduce vulnerabilities if not properly vetted for security. Software to integrate with other tools and applications that teams use can streamline workflows and reduce the need to switch between different applications.
IoT Devices:
IoT devices make M&A activities riskier as they have contributed to converging traditional IT with operational technology. The increased connectivity has increased attack surfaces and exposure to hackers, including competitive adversaries that may wish to steal confidential data or intellectual property, disrupt businesses, or sabotage mergers.
How to Protect Privacy in M&A
To mitigate these vulnerabilities, businesses should implement robust cybersecurity measures, including:
A Virtual Deal Room
A Virtual Deal Room (VDR), also called a virtual data room, is a cloud-based online platform that protects documents with robust security protocols. Choose a reputable and secure VDR provider that specializes in handling sensitive information and has a history in M&A. Look for features like data encryption, user permissions, activity tracking, and robust access controls.
A ShareVault VDR provides a secure workplace for an M&A team and its third-party contributors, with protections for team members in any location and using any authorized device, at any time. The M&A team project administrator can set time and content limits on access and can deauthorize access at any time.
Document Encryption
An encrypted document is safe from hackers and the competition—unlike a document created in Google Docs, Word, or other standard business word processing apps. With the proper safeguards, the document remains safe during both storage and transit.
With a quality provider like ShareVault, every document uploaded to the VDR is automatically encrypted with 256-bit encryption at the time when it is uploaded to the VDR. Files in transit are via HTTPS over Secure Sockets Layer (SSL), providing AES-256 encryption in transit.
Password Protection
Control over access to sensitive documents is essential. Only authorized personnel should have access to archived and work-in-progress documents.
ShareVault recommends use of two-factor passwords and Two-Factor Authentication (2FA), which requires users to provide a second form of identification, such as a code sent to their mobile device.
Strong Authentication Methods
Use a VDR with built-in features that allow the project administrator to set specific permissions for each user or group accessing private documents. Implement Role-Based Access Control (RBAC), a policy in which team M&A project team members are granted access to sensitive documents based on their roles and responsibilities; not everyone in the organization needs access to every sensitive document.
ShareVault permissioning protocols include passwords, device IP registration, and limits on rights of access and usage for every document, a combination of features that ensures documents are only accessible by the right people.
Document Tracking and Watermarking
The M&A project leader needs the ability to monitor access and usage. A quality VDR provider has built-in monitoring functions. Another useful security tool is digital watermarks, time-and-origin stamps on a document that can deter unauthorized sharing and help identify the source of any leaks.
- ShareVault user monitoring feature provides real-time updates of every document—who has accessed the document and what actions have been taken
- ShareVault monitoring reports can be generated at any time for audits by senior management or by regulatory agencies
- ShareVault provides a dynamic watermarking tool for any document in the VDR
Secure Communication Channels
As noted, email, file sharing apps, and other communication channels lack the enterprise-grade security of a VDR. Require M&A team members and their collaborators to restrict document archiving and sharing activities to the secure VDR environment.
Regular Security Updates and Patches
Keep all software and systems up to date with the latest security patches to prevent vulnerabilities that could be exploited. As the threat landscape continues to evolve, it’s crucial for businesses to stay informed about the latest cybersecurity best practices and regularly update their security protocols to protect sensitive data and collaboration channels.
Data Loss Prevention (DLP) Solutions
Consider using DLP solutions that can detect and prevent sensitive data from being shared inappropriately, either within the organization or outside of it.
Regular Security Training
Conduct regular security awareness training for employees to educate them about the importance of safeguarding sensitive documents and the potential risks associated with mishandling them.
ShareVault’s experienced support team can help team members with information and advice, and they are available 24/7/365.
Choose an Experienced, Quality VDR Provider
ShareVault has been the VDR of choice for more than $50 billion in M&A and finance transactions. In addition to its many security safeguards, ShareVault has software tools that streamline due diligence, including its Due Diligence Checklist, a software template that automatically populates a VDR with the most commonly used folders and sub folders.
Companies engaged in M&A also need to manage their budgets effectively. ShareVault offers a cost-effective solution for managing confidential data with flexible pricing plans that allow companies to choose a plan that suits their needs and budget. ShareVault's pricing is transparent, with no hidden costs, so there are never any surprises.
To receive a customized proposal, contact ShareVault today!
