Table of Contents
- The Importance of Virtual Privacy in Our Ever-Connected World
- The Nitty Gritty of Passwords: Creating Strong and Unique Codes
- Introducing VPNs: The Invisible Cloak of the Online World
- Email Safety 101: How to Send Sensitive Information Securely
- Mobile Security Measures: Guarding Your Pocket-Sized Powerhouse
- Bonus: Travel tips
- Social Media and Privacy: How to Navigate the Personal and Professional
- Browsing Safely: Keeping Your Online Exploration Secure
- Advanced Security Measures for Executives: Going the Extra Mile
- Key Takeaways
- The Future of Digital Security: Staying Ahead of the Curve
The Importance of Virtual Privacy in Our Ever-Connected World

In an era where we are all part of a grand digital tapestry, the importance of safeguarding our virtual privacy has reached an unprecedented level. This applies equally to you, the average internet surfer, as well as to the high-level executives operating in the corporate world.
Does it sound complicated? It could be. But doesn't it also sound important? You bet it does.
Consider this scenario:
It's Tuesday morning, and you're managing your personal finances from your favorite coffee shop. Concurrently, several floors up in a glass-tower building, an executive is finalizing the detail of a million-dollar deal. Both of these internet users—despite the difference in their activity's scale—are linked by one common thread: a need for virtual privacy.
Now, around the globe, from the trendiest start-ups to the most established corporations, securing private information has become a top priority. Breaches in virtual privacy can lead to negative consequences, from personal distress to corporate downfalls.
It's therefore essential for all internet users to understand and implement strategies to protect their privacy online.

Read on and learn how to protect your private information and create safeguards that will give you peace of mind and your business the security it needs. Because in this ever-connected world, privacy is a right, not a privilege.
And protecting it? That's a responsibility we all share.
The Nitty Gritty of Passwords: Creating Strong and Unique Codes

We already know the importance of having a solid password, but creating one that satisfies all the boxes for being "strong" and "unique" is a task that often leaves us scratching our heads in confusion.
Let's simplify.
First, your password should be long, ideally, 12 to 16 characters.
Why?
Because it makes it harder for hackers to simply guess your password using a method called 'brute force'. Understand it this way - your password is like a lock and the number of possible keys to that lock exponentially increases with the length of your password. Interesting, isn't it?
But having a long password isn't enough, you ask?
You're absolutely right.
The composition of your password is equally important. Here's a little trick for you - intermingle uppercase and lowercase letters, numbers, and symbols. That's right, give your password some personality!
Originality plays a huge role too.
Resist the urge to keep your birthday, pet's name, or favorite football team as your password. These personal details are easy to find (the world knows all about you already), leaving your account vulnerable. Instead, opt for an obscure phrase or quote, or maybe something whimsical that only you would understand, and sprinkle in some numbers and symbols for good measure.
Finally, make sure your passwords are unique across all platforms. Using the same password, while convenient, is akin to using the same key for your house, car, and safety deposit box. One breach, and everything you hold valuable is up for grabs.
Since all your accounts with passwords are now more than a few, this calls for another tool to help, a password manager. These apps can safely store your accounts and all the associated unique passwords.
Every time you access an older account, change the password to one that is "strong". This assures that all the previous passwords you used have now been stolen and cannot be used to ruin your day.
Be sure to turn on the extra verification step with two-factor authentication.

Introducing VPNs: The Invisible Cloak of the Online World

If you've ever wondered about slipping through the digital landscape undetected, a virtual private network, or VPN, can be your proverbial cloak of invisibility. But what is a VPN, and how does it enhance your online privacy?
What is a VPN?
A VPN is a technology that helps safeguard your data as it traverses the internet by creating a secure, encrypted tunnel between your device and the server you connect with. This ensures your internet connection is private and secure.

VPN technology is essential not just for the everyday user but also for businesses to keep their confidential information from falling into the wrong hands. However, it's crucial to remember that while VPNs enhance your online security, they are not infallible.
They function best in combination with other security practices, such as using strong passwords and maintaining up-to-date devices and applications.

Once you've grasped the VPN basics, the next step is choosing a VPN. Be sure to select one from a reputable provider with strong encryption capabilities, a no-logs policy, and robust security features.
Moving Forward with VPNs
Imagine a more secure, private internet browsing experience. That's the power of a VPN. With the information you've gathered here, you're now ready to navigate the world of virtual private networks confidently.
Remember, your online safety is paramount. In our interconnected world, a VPN is an indispensable tool for protecting that safety. So pull on your invisible cloak and journey through the digital realm with a sense of enhanced security.
Email Safety 101: How to Send Sensitive Information Securely

Email, while a practical and efficient communication tool, also serves as an integral pathway for transmitting private information. You should know how to navigate through email security properly to prevent unauthorized access while conveying sensitive data.
When sending private information via email, encryption is key. Encryption translates your data into a code, ensuring that only authorized recipients with the correct decryption keys can decode and read it.
This process helps prevent unwanted third parties from accessing your private information. Guidelines set out by the Federal Trade Commission (FTC) recommend using https, s/mime, or VPN for data encryption.
However, also ensure that the receiving party can decrypt your emails. Sharing encryption keys or passwords over the same email account or one that isn't secure can expose your data to potential security breaches. A secure method to share decryption tools might be over the phone or through encrypted, private messenger apps (source: FTC).
Further, make it a routine to regularly update your passwords, and avoid using obvious choices like birthdays, or easy-to-guess sequences like 12345. Regular updates and complex password choices can throw potential hackers off track, and keep your email account safer.
Lastly, be attentive to the content of your emails. Be wary of scam emails requesting sensitive information and think twice before clicking on links or downloading attachments from suspicious emails.

While you can't eliminate all online threats, these steps will significantly bolster your email protection strategy and ensure your sensitive information is much safer.
Mobile Security Measures: Guarding Your Pocket-Sized Powerhouse

Liminal space between your pocket and the world of the Internet, smartphones have truly revolutionized the way we access, store, and share information. But with great power, comes great vulnerability. Your phone contains a trove of sensitive personal information that can be misused if fallen into the wrong hands.
Now, before that prospect sends a chill down your spine, let's look at ways to ensure its safety.
Regular Software Updates: An Updated Phone is a Secure Phone
There's a reason why your phone continuously nags you to install those software updates. These updates often contain patches for security vulnerabilities that have been identified in your phone's operating system. Not updating your software is like leaving your keys under the mat; you're making it incredibly easy for cybercriminals to access your information.
Taking Advantage of Biometric Authentication
Imagine if your phone knew you, as intimately as a close friend or family member. Biometric authentication methods, like facial recognition and fingerprints, offer this advantage. Not only do they add an extra layer of security, but they are also incredibly convenient. In a world where time is as valuable as money, that's a win-win.
Enabling Two-Factor Authentication: Double Trouble for Intruders
Two-factor Authentication (2FA) provides an extra layer of security. Even if someone manages to guess your password, guess what? They still can't get in! By adding this extra hurdle, you substantially lower your risk of being hacked. It might seem tedious at times, but remember, safety often comes at the cost of convenience.
App Downloading: Making Wise Choices
There's virtually an app for everything these days. But not all apps are created equal. Some may be Trojan horses harboring malware or spyware, ready to compromise your personal information. Stick to official stores like Google Play or Apple app store for downloads and always check an app's reviews and permissions required before hitting that install button.
Wi-Fi and Bluetooth: The Invisible Channels of Insecurity
Wi-Fi and Bluetooth are two of the greatest conveniences of modern technology, but they can also be significant security vulnerabilities. Intruders can snoop in on your online activity through unsecured connections, accessing sensitive data. Always turn off these features when not in use and refrain from connecting to unknown or public networks.
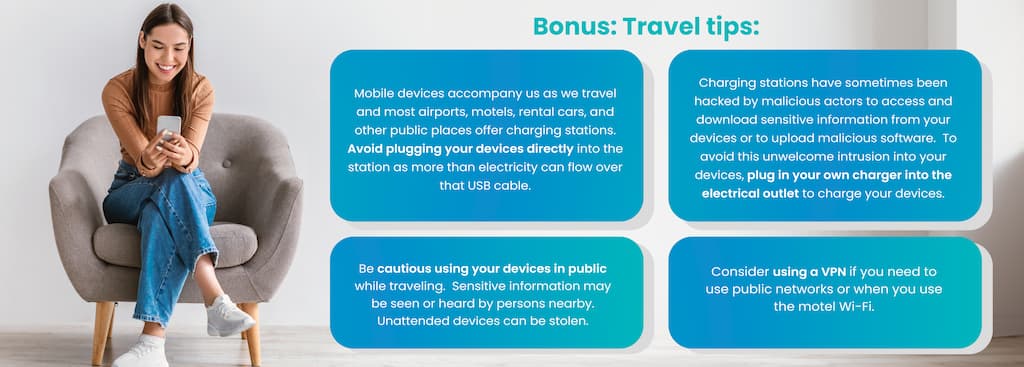
Bonus: Travel tips:
Social Media and Privacy: How to Navigate the Personal and Professional

As an internet user or a corporate executive, understanding the intricate balance between personal relations and professionalism on social media is key. These platforms are undoubtedly an excellent way of connecting the world, but they also pose significant privacy challenges if not appropriately managed.
Facebook: Facebook is the father of all social media platforms, but with this popularity comes security risks. When using Facebook, ensure you're only accepting friend requests from people you trust. Always limit what information is publicly viewable and regularly revisit your privacy settings to ensure they're up to date.
Twitter: Twitter is infamous for its open conversation style, which can be great for sharing ideas, but also means your tweets are publicly visible unless protected. You can mitigate risks by avoiding sharing sensitive personal or professional information.
LinkedIn: Navigate LinkedIn with caution, despite its professional presentation. Don't share sensitive job or business details and only connect with people you know or trust. It's also important not to fall for fake job offers or phishing messages often sent through LinkedIn's messaging system.
Instagram: Instagram is visually captivating, but it could also expose more information than you'd like, through pictures and stories. Go through your follower list regularly to ensure they are all trusted individuals or brands. Its geolocation feature should also be used carefully due to privacy concerns.
Snapchat: Snapchat's disappearing content seems ephemeral, but remember, screenshots exist. Only send snaps to trusted recipients, and pause before posting anything on the Snap Map which publicly shows users' locations.
Be proactive, set strong privacy settings, and be aware of what you are posting and to whom. After all, the main mantra for operating securely online remains, "Think before you share."
Browsing Safely: Keeping Your Online Exploration Secure

As you navigate the labyrinth of the internet, your choice of search engine matters more than you might think. It's not just about speed or user interface; it's also about the capacity to protect your personal data and browsing habits from prying eyes. In this section, we'll cover prominent search engines and their commitment to your online security.
Google: Google is the most widely-used search engine. Beyond its speed and efficiency, Google does offer some security features. With safe search filtering, Google flags or removes potentially harmful sites from your search results. It also offers incognito mode, which doesn't save your browsing history, although it doesn't make your activity invisible.
Bing: Bing, Microsoft's entry in the search engine arena, carries over the company's commitment to security. Bing offers safe search features like identifying potentially harmful websites and deleting user history after a specified time period.
DuckDuckGo: For those desiring maximum privacy, DuckDuckGo is a potent option. It excels in protecting user's data and doesn't track your browsing history or sell your data to advertisers. Although the user interface may be simplistic, the commitment to privacy makes DuckDuckGo a preferred choice for the security-conscious.
StartPage: StartPage uses Google's search technology but adds an extra layer of privacy, as it does not record IP addresses or track user behavior. It offers an anonymous view feature that allows users to browse other websites without being tracked.
When it comes to selecting a search engine, prioritize privacy and security features over-familiarity or convenience. And remember, pair your secure search engine with other protective measures like a VPN or Tor for optimum online security.
Advanced Security Measures for Executives: Going the Extra Mile

Virtual Data Rooms (VDR), such as Sharevault, offer the next level of online data protection. These secure online repositories offer a safe space to store, manage and share sensitive data. Let's dive deeper into their significance and how they can serve as a fort of protection for your confidential information.
Understanding Virtual Data Rooms
VDRs are essentially digital warehouses where data can be securely stored and accessed. They provide a highly secure, access-controlled environment where sensitive documents can live, and only approved users can access them. Sharevault is among these secure VDRs, offering an extra layer of protection while sharing sensitive files.
Why Choose Sharevault?
Sharevault is a top-tier VDR that provides advanced security features. This includes Watermarking to deter unauthorized copying, Document Control to limit file access and the unique 'Shred' feature that allows the owner to remotely delete a downloaded file. Sharevault is an apt choice for executives who require exceptional security measures for their sensitive data.
Employing VDRs for Enhanced Collaboration
VDRs are not just about security - they also enable seamless collaboration. With Sharevault, users can easily share and co-edit documents while maintaining rigorous data privacy. This makes it ideal for tasks that involve multiple participants, such as project collaborations, financial transactions, legal proceedings, or even M&A due diligence processes.
Getting Started with Sharevault
Setting up your Sharevault account is user-friendly. You can begin by setting up a secure environment, adding users and controlling their permissions, and finally, uploading your sensitive documents. Remember, it doesn't substitute for standard security measures — rather it's the extra mile you go for optimised data protection.
By integrating VDRs like Sharevault into your digital security strategy, you not only ensure standard safety protocols are met, but you prioritise information security and pave the way for effective, secured collaboration.
Key Takeaways

Let's swiftly traverse down memory lane to summarize what we covered in the field of online safety:
- Our foray into the digital safety landscape commenced with an investigation into the crucial significance of virtual privacy in our perpetually connected globe. From there, we focused on the art of constructing robust and unique passwords, an elemental building block of your digital defenses.
- We then introduced the concept of Virtual Private Networks (VPNs), your personal invisibility cloak in the online world. By understanding their key features and how to move forward with them, your online footprint can become significantly more secure.
- Recognizing that the mobile realm is a world in itself, we further explored various mobile security measures to protect your pocket-sized powerhouse. Emphasizing on regular software updates, complex but versatile password management, biometric authentication utilization, two-factor authentication activation, wise app downloading, and the often overlooked channels of vulnerability - Wi-Fi and Bluetooth. Each serves as a part of the wider framework that, when used in unison, fortifies your mobile device's defense system.
- As we shifted to the frequently trodden ground of social media, we unlocked the key to maintaining privacy while navigating the personal and professional borders. And let's not forget the importance of browsing securely. In our interconnected world, each link clicked or browsed can present a potential vulnerability - learning how to steer clear of these pitfalls will certainly benefit you.
- In the context of corporate scenarios, we went up a level to discuss advanced security measures for executives. Efficient solutions such as Virtual Data Rooms and Sharevault's services can substantially enhance collaborative efforts, stepping up both productivity and security.
The Future of Digital Security: Staying Ahead of the Curve
Ultimately, the future of digital security is bright and hopeful-filled, if you're willing to keep pace. By implementing what's been discussed, staying vigilant, and anticipating future trends, you can be confident about your security in the online sphere. The challenge is robust, but the rewards of a secure digital life are worth it.
