In today's rapidly evolving digital landscape, businesses and organizations deal with an abundance of sensitive information that requires rigorous protection. Virtual data rooms (VDRs) have emerged as essential tools for securely managing and sharing confidential data, especially during critical processes like mergers and acquisitions, due diligence, legal proceedings, and financial transactions. One of the paramount aspects of any reliable VDR is its robust data encryption and protection features, ensuring that data remains secure throughout its lifecycle.
Understanding Virtual Data Rooms
Virtual data rooms are online repositories designed to store, manage, and share sensitive documents and files. They have largely replaced physical data rooms due to their convenience, efficiency, and enhanced security features. Virtual data rooms are used across various industries, including finance, healthcare, legal, real estate, and more, to facilitate secure information exchange among authorized parties.
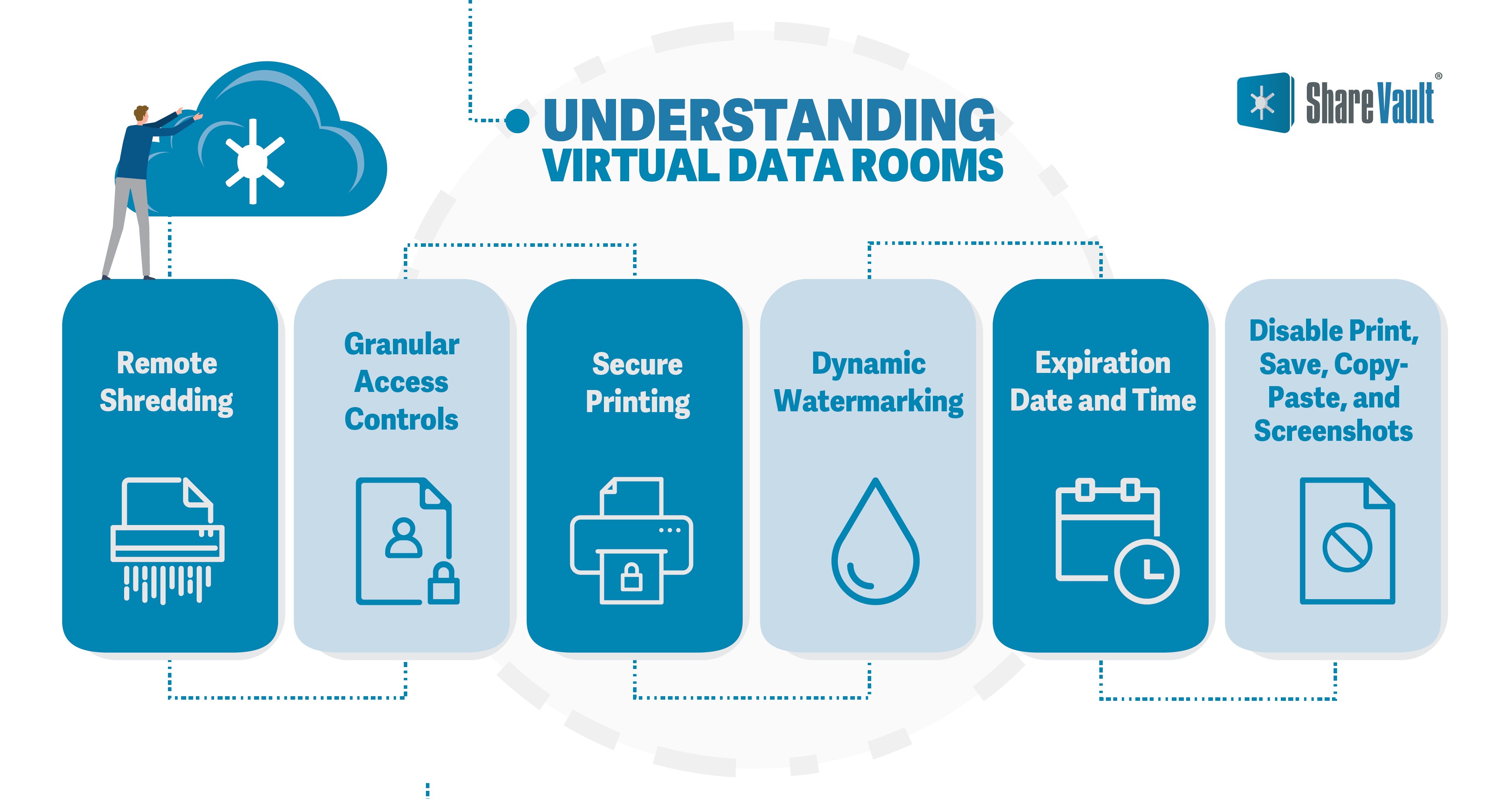
Many state-of-the-art virtual data rooms offer advanced document security features such as:
- Remote Shredding: The ability to revoke a user’s rights to view a document, even after it’s been downloaded.
- Granular Access Controls: The ability to customize document security policies by user, group, and folder.
- Secure Printing: The ability to prevent users from printing to PDF, even if physical printing is permitted.
- Dynamic Watermarking: Watermarks can be applied to every page of a document, identifying the user and effectively deterring them from unauthorized distribution of the document.
- Expiration Date and Time: Admins can enforce deadlines by setting a date/time when a document can no longer be opened.
- Disable Print, Save, Copy/Paste, and Screenshots: Secure countermeasures for ultimate document sharing protection.
Data Encryption: The Cornerstone of Security
Data encryption is the process of converting plain text data into a complex cipher text format using cryptographic algorithms. This transformation ensures that even if unauthorized individuals gain access to the data, they cannot decipher it without the proper decryption key. Modern virtual data rooms employ advanced encryption techniques to safeguard data integrity and confidentiality. Key encryption features include:
End-to-End Encryption
End-to-End Encryption (E2EE) is a security concept and communication protocol designed to ensure that the content of a message or data remains private and secure throughout its entire journey between the sender and the intended recipient. The primary goal of end-to-end encryption is to prevent unauthorized access, interception, or eavesdropping by anyone, including service providers, hackers, or even government agencies.
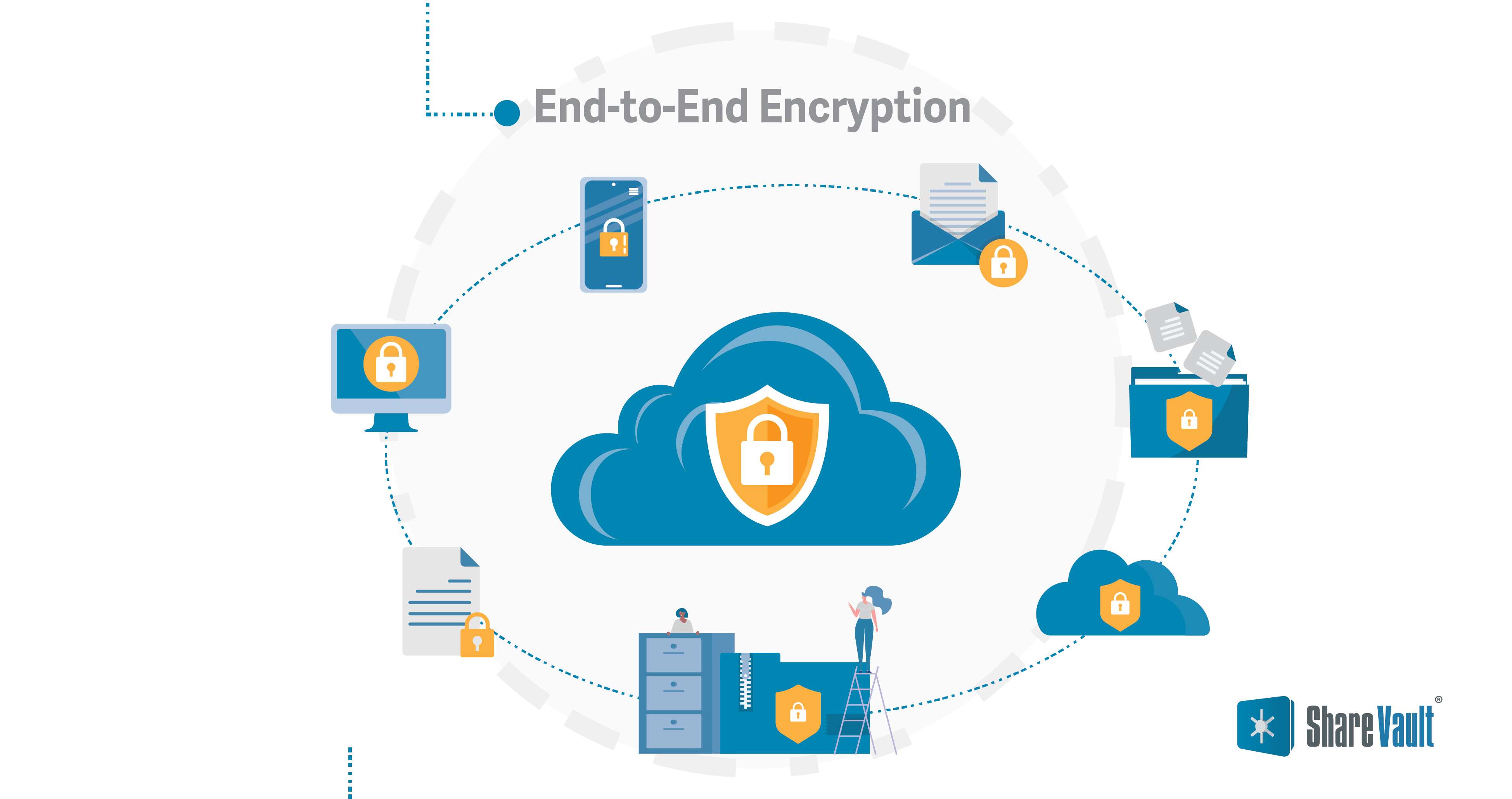
In a system with end-to-end encryption, the encryption and decryption processes occur exclusively on the sender's and recipient's devices, known as the endpoints. This means that even the service provider facilitating the communication cannot access the content of the message in a readable form. The data is encrypted by the sender's device and can only be decrypted by the recipient's device, ensuring that any intermediate servers or entities cannot decipher the information.
Here's how the process generally works:
- Encryption: When a user sends a message or data, their device applies encryption to the content before it leaves the device. This encryption transforms the original content into an unreadable format using encryption keys.
- Transmission: The encrypted data is then transmitted over the network to the recipient's device or server.
- Decryption: Upon receiving the encrypted data, the recipient's device applies decryption using a corresponding decryption key, which converts the encrypted data back into its original readable form.
The term "end-to-end" refers to the fact that the data is only decrypted at the endpoints—the devices of the sender and the recipient. Any intermediary points, such as servers or routers, only see the encrypted data and cannot access the content.
256-bit AES Encryption
256-bit AES (Advanced Encryption Standard) encryption is a widely used symmetric encryption algorithm that provides a high level of security for protecting sensitive data. AES was established as the successor to the older DES (Data Encryption Standard) and 3DES (Triple DES) algorithms, both of which had become vulnerable to modern cryptographic attacks due to their relatively small key sizes.
AES operates on blocks of data and supports key lengths of 128, 192, and 256 bits. The number in the key length (128, 192, or 256) indicates the size of the key used for encryption and decryption. Among these options, 256-bit AES encryption employs the longest key length and is considered the most secure variant.
Here's how 256-bit AES encryption works:
- Key Generation: The encryption process starts with generating a 256-bit key. This key is used both for encryption (making data unreadable without the key) and decryption (recovering the original data with the key).
- Subkey Generation: The 256-bit key is expanded into a set of round subkeys using a key expansion algorithm.
- Encryption Rounds: AES encryption operates on blocks of data (typically 128 bits). Each round consists of several transformations, including substitution, permutation, and mixing operations. The exact number of rounds depends on the key length: 10 rounds for 128-bit keys, 12 rounds for 192-bit keys, and 14 rounds for 256-bit keys.
- Substitution and Permutation: In each round, AES performs a substitution step (replacing each byte of the data with another using a predefined substitution table) and a permutation step (rearranging the bytes in a specific way).
- Mixing Operations: AES also includes mixing operations to ensure that different parts of the data influence each other, increasing the overall security.
- Final Round: The final round omits the mixing step to simplify decryption.
Data Segmentation
Virtual data rooms often offer the ability to segment data into specific categories or groups. This allows administrators to apply different encryption levels and access controls to various types of data, adding an extra layer of protection.
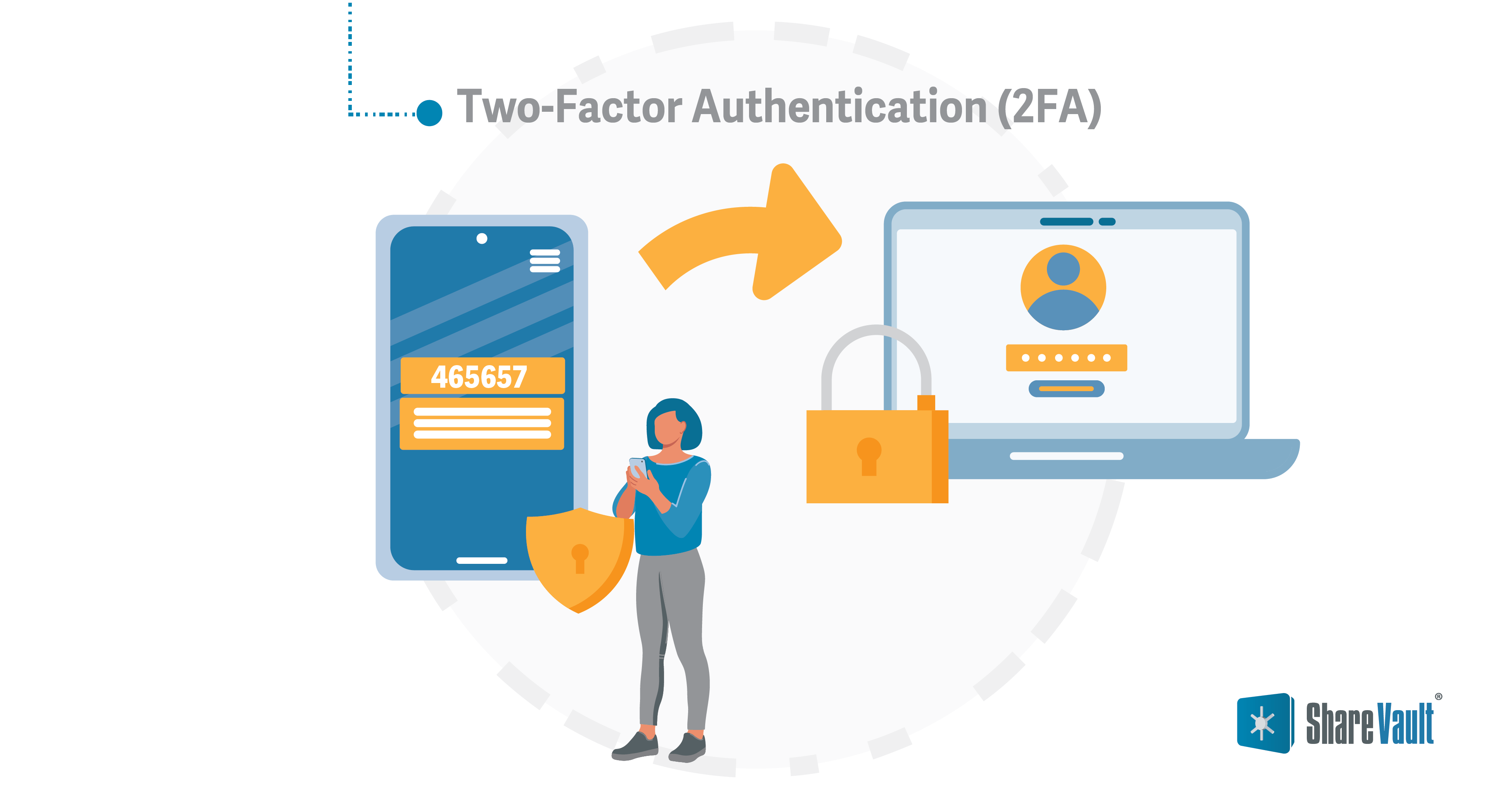
Two-Factor Authentication (2FA)
While not strictly an encryption method, 2FA adds an additional security layer by requiring users to provide two forms of identification before accessing the data room. This prevents unauthorized access, even if login credentials are compromised.
Granular Access Controls
VDRs enable administrators to define precisely who can access certain documents and files. With fully-configurable file security policies, administrators can define the appropriate levels of file protection. For each policy, administrators can specify whether or not users have the right to print, save, copy/paste text, capture the screen, and which, if any, watermark should be applied. In addition, thay can specify an absolute or relative expiration date. Much more flexible than the limited view/print/save levels provided by a typical virtual data room, these advanced security policies give administrators the ability to easily control exactly what rights each user has when accessing content. And, because it's so easy to change, admins can modify a user’s rights as the project progresses.
Dynamic Watermarking
To deter unauthorized document distribution, modern VDRs often include dynamic watermarking features. Watermarks are clearly visible, applied diagonally across the page or screen, yet do not interfere with the readability of the underlying text. The watermark text is customizable, and you can embed the following dynamic information:
- User's email address
- User's IP address
- Current date
- Current time
Watermarks provide a clear indication to the reader that the content is confidential, and since the user identity can be included in the watermark, it allows for a simple but effective deterrent against distribution of the printed documents to unauthorized readers.
Continuous Monitoring and Audit Trails
Beyond encryption, modern virtual data rooms offer robust monitoring and auditing capabilities. These features help track user activities within the data room, ensuring accountability and transparency. Audit trails provide a comprehensive list of every user login, agreement clickthrough, video watched or document viewed, printed or downloaded, with comprehensive specificity. Administrators can trace the chronology of activities by user and gain insights into their interest level and what they care about.
This same level of detail is applied to all administrative activities as well, to give administrators everything they need to backtrack security and configuration changes and effortlessly respond to any audit.
Secure Collaboration
Collaboration is a key aspect of VDRs, and encryption plays a pivotal role in enabling safe collaboration. Secure collaboration features include:
- Document Versioning: Encryption ensures that each version of a document is protected, allowing authorized users to collaborate on files without compromising security.
- Real-time Notifications: Users are alerted when new documents are uploaded or changes are made, facilitating seamless collaboration while maintaining control.
- Secure Q&A and Messaging: VDRs often provide secure communication channels within the platform, allowing participants to discuss sensitive matters without resorting to less secure external communication methods.
Conclusion
In an era marked by data breaches and cyber threats, the importance of robust data encryption and protection features cannot be overstated. Modern virtual data rooms have risen to the challenge, employing state-of-the-art encryption methods and comprehensive security measures to ensure the confidentiality, integrity, and accessibility of sensitive information. As businesses continue to rely on virtual data rooms for critical operations, their ability to safeguard data through encryption remains a cornerstone of their effectiveness and relevance in today's data-driven world.
ShareVault has been providing organizations of all types and sizes with document security solutions for over 15 years.
