In the ever-evolving world of cybersecurity, staying ahead of threats and protecting sensitive data has become paramount. One approach gaining significant attention is the implementation of a Zero Trust framework.
Zero Trust Cybersecurity focuses on the idea that no user or device should be inherently trusted, regardless of their location or network access. To bolster the effectiveness of this approach, organizations are turning to micro-segmentation, a powerful technique that provides granular control over network resources. Let's take a look at the concept of micro-segmentation and how it strengthens Zero Trust Cybersecurity.
Understanding Zero Trust Cybersecurity
Traditional cybersecurity models often rely on perimeter-based defenses, assuming that threats can be kept out by securing the network boundary. However, the rise of advanced persistent threats (APTs) and sophisticated attacks have rendered this approach insufficient. Zero Trust Cybersecurity, on the other hand, adopts a more comprehensive and proactive approach.
Zero Trust operates under the assumption that no user or device should be inherently trusted, regardless of their location or network access. It emphasizes verification and continuous monitoring of all users, devices, and network activities. This approach ensures that every resource request and communication is treated as potentially malicious until proven otherwise.
Introduction to Micro-Segmentation
Micro-segmentation is a technique that complements the principles of Zero Trust Cybersecurity. It involves dividing the network into small, isolated segments or zones, each with its own unique security policies and access controls. By creating these virtual perimeters, organizations can contain lateral movements of threats and limit the potential impact of a breach.
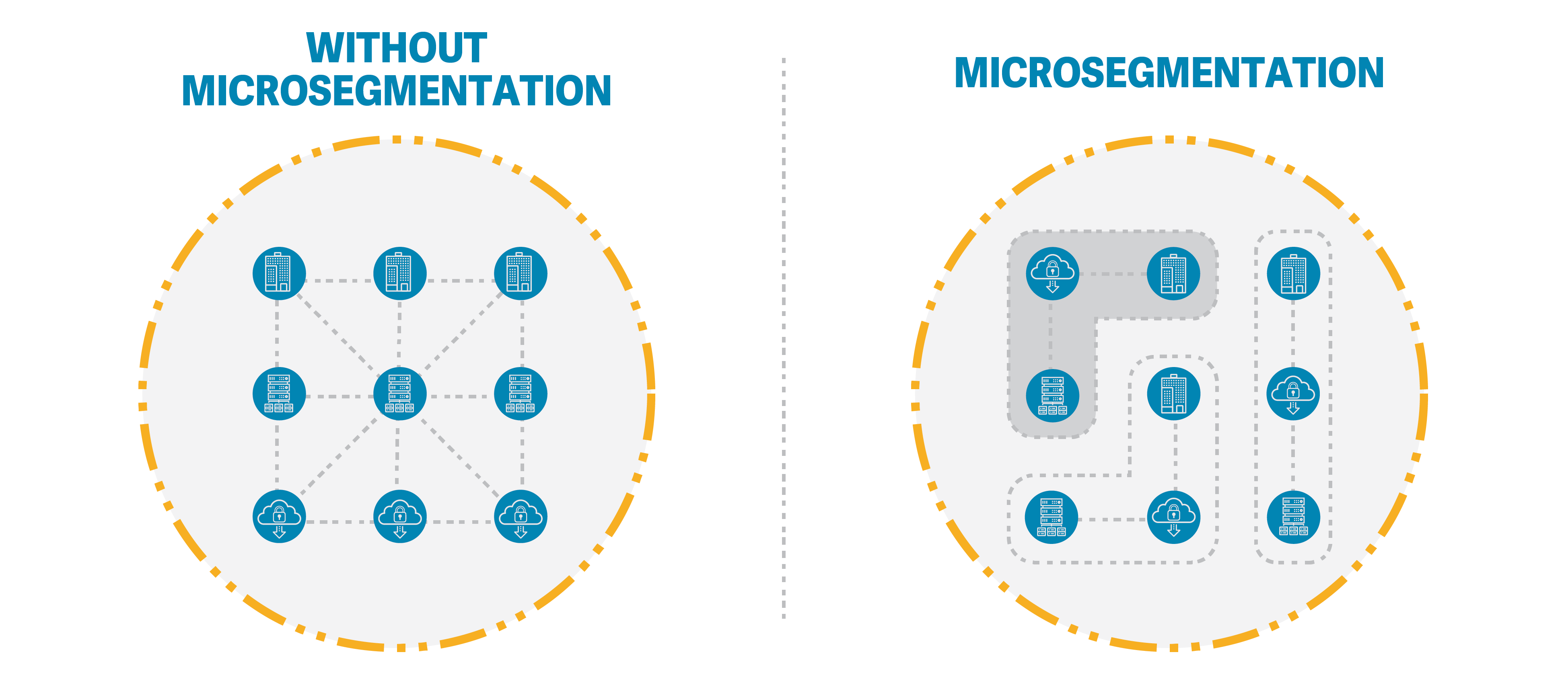
Benefits of Micro-Segmentation in Zero Trust Cybersecurity
Enhanced Security: Micro-segmentation provides a robust layer of defense by isolating critical assets and sensitive data. Each segment can have its own set of security policies, enabling organizations to restrict access to only authorized users and devices. This level of granularity minimizes the attack surface and mitigates the risk of lateral movement within the network.
Least Privilege Access: Micro-segmentation aligns perfectly with the principle of least privilege access. It ensures that users and devices have access only to the specific resources they need to perform their tasks. By tightly controlling access rights, organizations can minimize the potential for privilege escalation and unauthorized access to sensitive information.
Compliance and Regulatory Requirements: In many industries, compliance with various regulations is mandatory. Micro-segmentation facilitates compliance efforts by enforcing access controls and monitoring network activities. It allows organizations to demonstrate auditable controls and effectively protect sensitive data, ensuring adherence to regulatory standards.
Simplified Incident Response: In the event of a security incident, micro-segmentation aids in incident containment and response. Since each segment operates independently, isolating compromised systems becomes more manageable. Security teams can easily detect abnormal behavior within a specific segment and swiftly respond, preventing the lateral spread of threats.
Scalability and Flexibility: Micro-segmentation can adapt to evolving network architectures and business requirements. Whether organizations operate on-premises, in the cloud, or across hybrid environments, micro-segmentation can be implemented consistently. This flexibility enables seamless integration with existing infrastructure and supports future growth and technological advancements.
Implementation Considerations
Implementing micro-segmentation within a Zero Trust framework requires careful planning and consideration. Here are some key factors to keep in mind:
Understand Your Network
Before implementing micro-segmentation, it's essential to have a thorough understanding of your network's architecture, including:
- The types of devices connected to your network
- Data flows and communication patterns within your network
- Critical assets and data that need protection
- Existing security policies and measures in place
This knowledge will serve as the foundation for designing your micro-segmentation strategy.
Identify Critical Assets and Data
Identify and prioritize your organization's critical assets and sensitive data. This could include customer information, intellectual property, financial records, or proprietary software. By classifying data and assets, you can determine which segments need the highest level of security and which can have more permissive policies.
Plan Your Segmentation Strategy
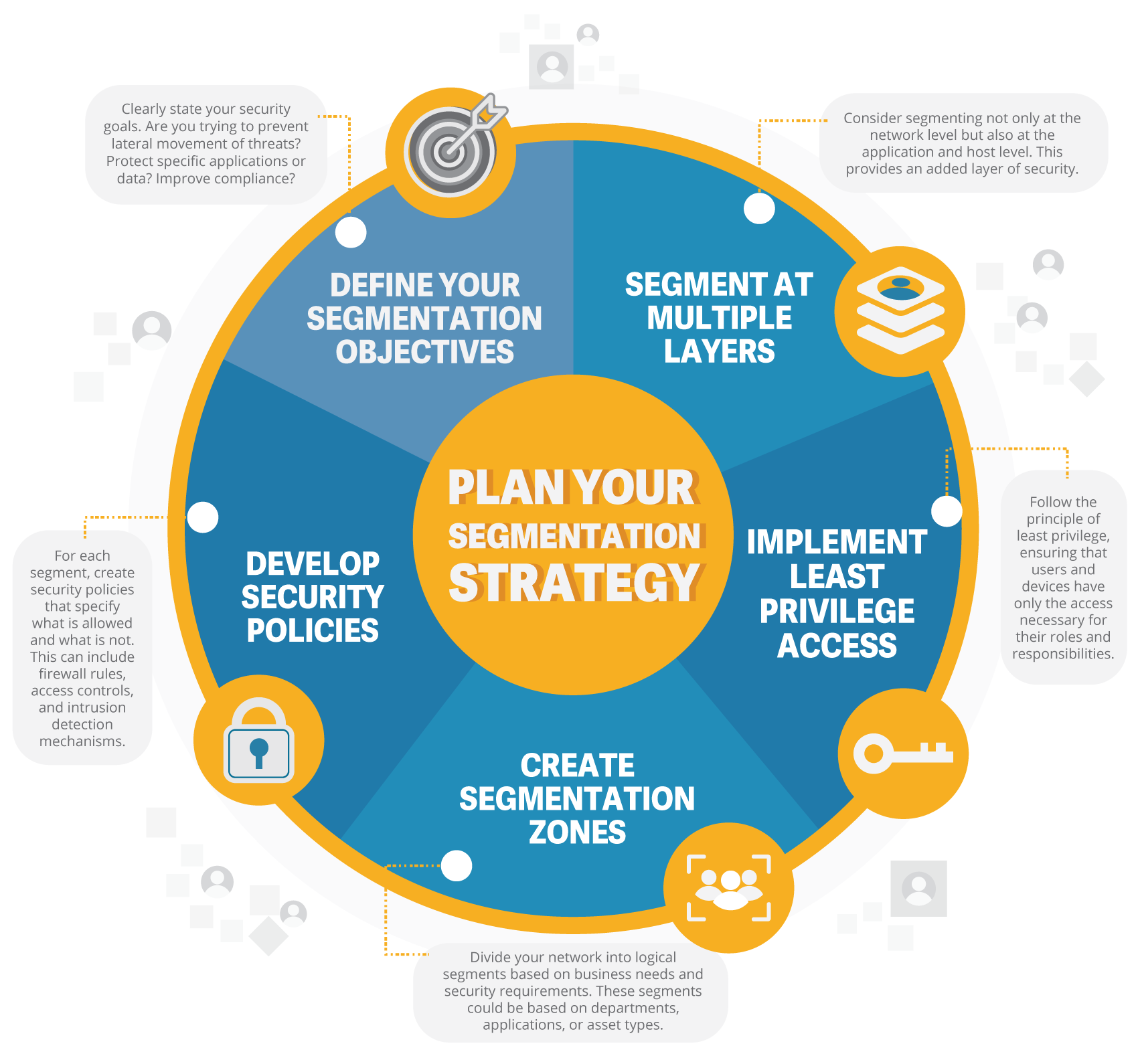
Designing a micro-segmentation strategy requires careful planning. Consider the following steps:
- Define Your Segmentation Objectives: Clearly state your security goals. Are you trying to prevent lateral movement of threats? Protect specific applications or data? Improve compliance?
- Create Segmentation Zones: Divide your network into logical segments based on business needs and security requirements. These segments could be based on departments, applications, or asset types.
- Develop Security Policies: For each segment, create security policies that specify what is allowed and what is not. This can include firewall rules, access controls, and intrusion detection mechanisms.
- Implement Least Privilege Access: Follow the principle of least privilege, ensuring that users and devices have only the access necessary for their roles and responsibilities.
- Segment at Multiple Layers: Consider segmenting not only at the network level but also at the application and host level. This provides an added layer of security.
Choose the Right Tools
Select the appropriate technology to implement micro-segmentation. Some popular options include:
- Firewalls: Next-generation firewalls with application-aware features can enforce policies at the network perimeter.
- Software-Defined Networking (SDN): SDN solutions allow for dynamic network configuration and can facilitate micro-segmentation.
- Micro-Segmentation Solutions: There are specialized micro-segmentation tools and platforms designed to simplify the implementation and management of micro-segmentation policies.
Implement and Test
Once you've designed your micro-segmentation strategy and chosen your tools, it's time to implement and test your policies. Follow these steps:
- Deploy the necessary infrastructure and configure your chosen tools.
- Gradually roll out micro-segmentation to avoid disruptions. Start with less critical segments and gradually expand.
- Continuously monitor and test your policies for effectiveness. Adjust policies as needed based on real-world usage and emerging threats.
Educate Your Team
Ensure that your IT and security teams understand the micro-segmentation policies and know how to manage and troubleshoot them effectively. Training is key to successful implementation.
Monitor and Maintain
Micro-segmentation is not a one-time task; it requires continuous monitoring and maintenance. Regularly review and update your policies as your network evolves. Stay informed about emerging threats and vulnerabilities that may require policy adjustments.
Conclusion

Micro-segmentation is a vital component of an effective Zero Trust Cybersecurity strategy. By dividing the network into isolated segments, organizations can significantly enhance their security posture.
The fine-grained control over access and the isolation of critical assets ensure that even if a breach occurs, its impact can be contained. With its numerous benefits, micro-segmentation provides organizations with a proactive defense against evolving threats and enables compliance with regulatory requirements.
By adopting micro-segmentation within a Zero Trust framework, organizations can fortify their cybersecurity defenses and protect sensitive data from increasingly sophisticated attacks.
ShareVault has been providing organizations of all types and sizes with secure document sharing solutions for over 15 years.
